In addition to OAuth 2.0 (with Open ID Connect), TeamForge supports SAML (Security Assertion Markup Language) authentication and authorization protocol.
As in a typical SSO-enabled environment, Single Sign-on in TeamForge works in such a way that the Identity Provider "asserts" the identity of the user and the Service Provider consumes the "assertion" and passes the identity information to the application. This is done by exchanging digitally signed XML documents.
TeamForge, as a SAML compliant Service Provider, can be integrated with any SAML compliant Identity Provider. TeamForge Administrators should make sure that the Identity Provider is SAML 2.0 compliant and must keep the IdP metadata handy before configuring the IdP details in TeamForge.
- The Service Provider metadata XML file contains the SP certificate, the entity ID, ACS parameters and so on. To get the TeamForge (Service Provider) metadata, check at: https://<<hostname>>/oauth/metadata.jsp
- The Identity Provider metadata XML file contains the IdP certificate, the entity ID, redirect URL, logout URL and so on.
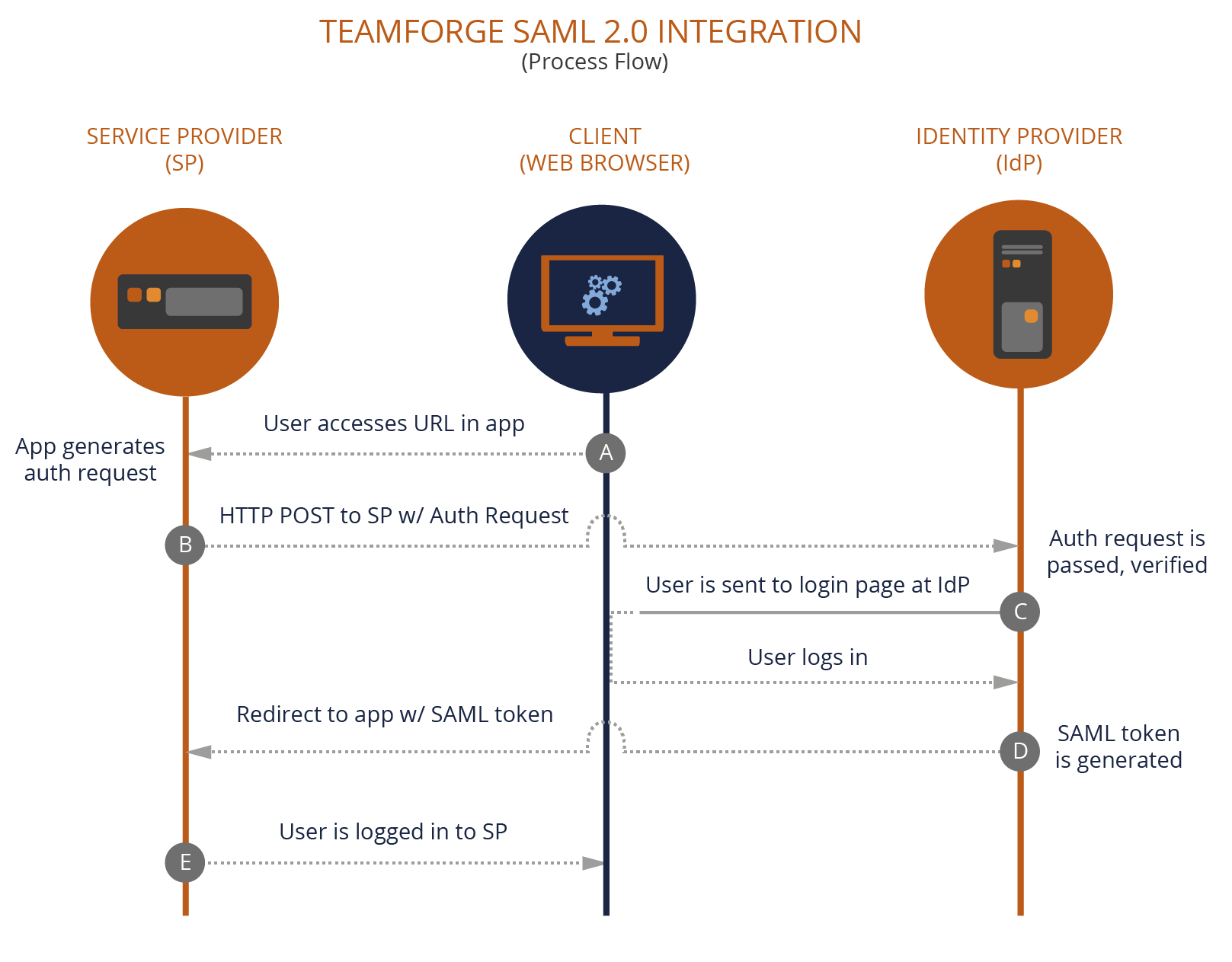
- The end user tries to access a resource URL within the application provided by the Resource Server (Service Provider) via the Client application / Web Browser (A).
- The Resource Server application generates the authentication request for user and sends it to Authorization Server (Identity Provider). The Service Provider uses the HTTP POST binding component to send the request to the IdP (B).
- If the authentication is successful, the user is redirected to the Authorization Server's (IdP) login page, through which the user logs in (C).
- The IdP generates the security token based on SAML assertions for the user and sends the response with the SAML token to the Resource Server application (D).
- The user now gets a session in the Resource Server and can access the resources in it.