In an Isolated-Access Deployment, each Client node is on a Network Address Translation (NAT) network behind its Lab Management Manager.
That is, all network traffic to and from the Isolated-Access network is routed through the Lab Management Manager. Users must create tunnels through the Lab Management Manager to access Client nodes. You can see the Lab Management Manager from the outside because of its routable IP address but you cannot see the private Lab Management subnets from the outside.
The characteristic of an Isolated-Access Deployment is that the Lab Management Manager has one IP address on the routable network and one IP address on each non-routable subnet.
Individual ports and Web Services located on Isolated-Access Client nodes can be exposed through two features in the Lab Management Web Console:
- Port Forwarding
- Host URL Mapping
Using these two features, administrators can selectively and safely expose all types of services out of their Isolated-Access networks.
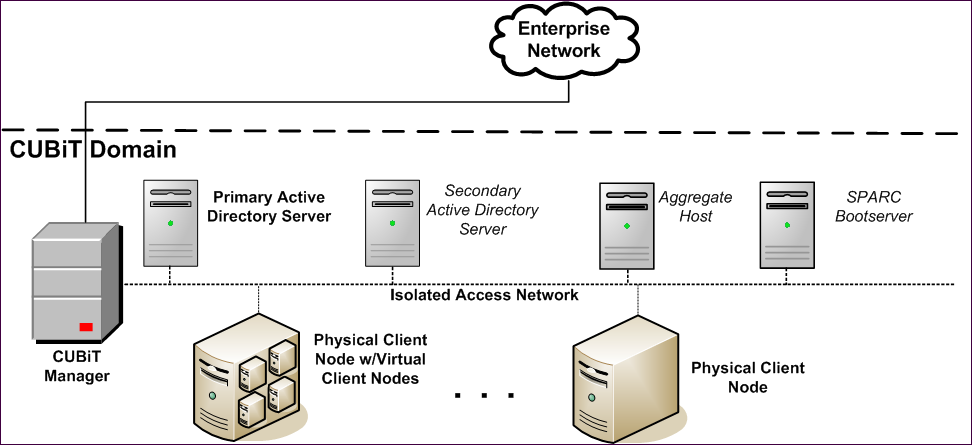
Example of an Isolated-Access deployment
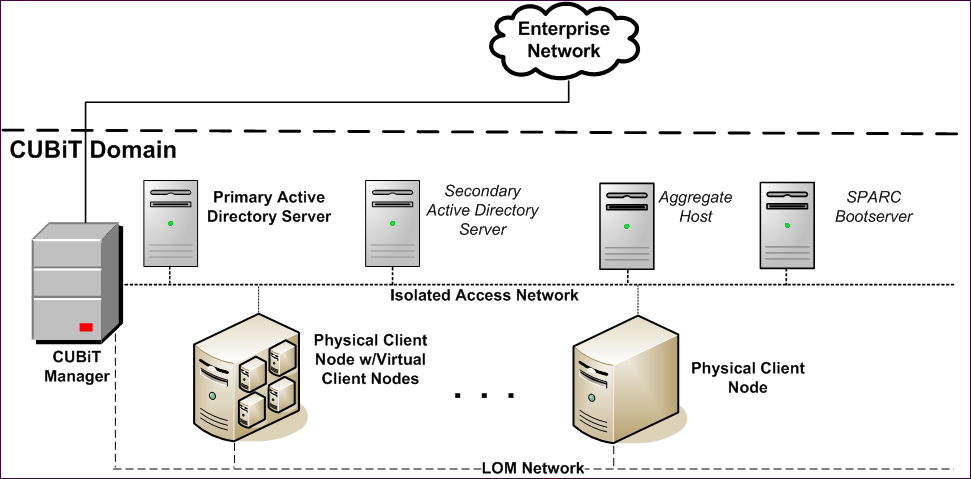
Example of an Isolated-Access deployment with a LOM network
If a company is deploying Lab Management in a QA environment and wants to isolate a segment of its network, then adopting the Isolated-Access Deployment schema might be a better approach. Traffic loads can be dictated without worrying about overloading other areas of the network.
Lab Management users and software developers typically prefer a Direct-Access Deployment because it is easier for them to access their systems. You can still achieve network isolation in a Direct-Access Deployment using a careful application of router Access Control Lists (ACLs). This type of information, however, is beyond the scope of this document.